Strategies for Planning Data-Driven IoT Architectures
When planning data-driven IoT architectures, adopting the right strategies is essential to simplify development, manage complexity, and ensure your solutions are scalable, flexible, and robust. This case study explores key strategies that can guide your approach:
- Use a layered architecture
- Integrate security by design
- Automate operational workflows
- Design for interoperability
- Leverage reference architectures
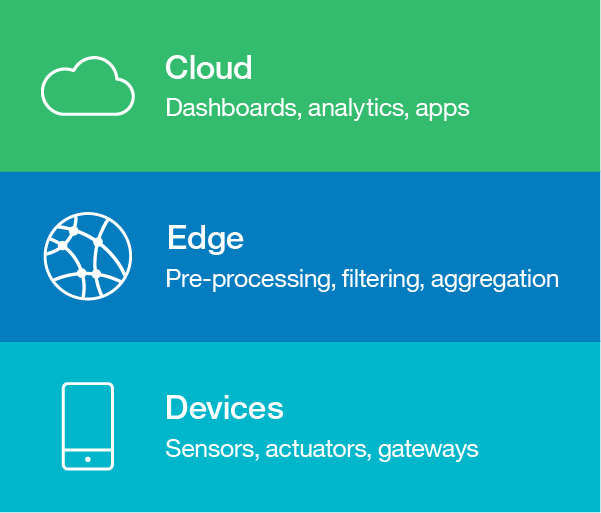
Selecting an appropriate architecture provides a clear blueprint for your IoT solution, defining both its physical components—such as sensors and actuators—and virtual components, including services and communication protocols. A modular, tiered approach to architecture helps manage the inherent complexity of IoT systems. For applications involving edge analytics, a common model includes three main tiers: device, edge, and cloud. This structure supports the seamless flow of data—from the physical devices, through localized edge processing, and onward to cloud-based services.
To address cross-cutting concerns, more advanced architectures incorporate vertical layers that span the entire system. These layers include identity management, access control, and data security—critical elements for ensuring system integrity and compliance.
Delegating workloads to the edge of the network—close to where data is generated—enhances performance by reducing latency, preserving privacy, and minimizing bandwidth consumption. This is especially important in real-time or bandwidth-sensitive applications.
Designing a successful data-driven IoT architecture requires more than just connecting devices to the cloud. It demands a thoughtful strategy that accounts for scalability, flexibility, security, and operational efficiency. This case study outlines five foundational strategies you can apply to streamline development and build robust IoT systems that deliver long-term value.
- Adopt a Layered Architecture
A layered architecture provides a structured way to organize your IoT system by separating concerns across different levels. This modular design simplifies development and maintenance while allowing different teams to work independently on each layer. At a basic level, a three-tier architecture includes:
- Device Layer: Consists of sensors, actuators, and embedded hardware responsible for data collection and interaction with the physical world.
- Edge Layer: Performs local processing, filtering, and analytics near the data source, enabling real-time decisions and reducing the load on central systems.
- Cloud Layer: Offers centralized services for data storage, advanced analytics, machine learning, and business intelligence. By clearly defining responsibilities at each layer, you can better manage system complexity and optimize resource use.
- Implement Security by Design
IoT ecosystems are highly distributed and vulnerable to various threats. Security must be integrated from the ground up rather than added as an afterthought. A "security by design" approach includes:
- Device authentication and encryption: Ensure only trusted devices connect to your network and encrypt data both in transit and at rest.
- Secure boot and firmware updates: Prevent unauthorized code from running on devices and maintain integrity through signed updates.
- Zero-trust architecture: Treat all devices, services, and users as untrusted until verified.
You should adopt standards and best practices for these aspects of your IoT infrastructure:
- Device, application and user identity
- Authentication, authorization (2FA), and access control based on roles
- Cryptographic Keys and Certificate management
- Secure communication channels and message integrity (by using encryption)
- Continuous telemetry data for monitoring the health of the devices
- Frequent auditing
- Classification of confidential and sensitive data, encrypted storage.
- Protocol security, secure delivery of updates Security should also extend across vertical layers, such as identity management, access control, and audit logging, to provide comprehensive protection at every stage of the data lifecycle.
- Automate Operations
Managing a large-scale IoT system manually becomes impractical as the number of devices grows. Automation helps you maintain consistency, reduce human error, and respond quickly to system events. Key areas to automate include:
- Device provisioning and onboarding
- Configuration management and updates
- Monitoring and alerting for failures or anomalies
- Data lifecycle management, including archival and deletion policies Using infrastructure-as-code (IaC) tools and centralized orchestration platforms can further accelerate deployment and ensure repeatability across environments.
- Design for Interoperability
IoT ecosystems are often heterogeneous, consisting of different devices, platforms, and protocols. Designing for interoperability enables your solution to work across vendors and ecosystems, unlocking flexibility and future-proofing your investment. To support interoperability:
- Use open standards like MQTT, CoAP, and OPC UA.
- Adopt API-first design to enable seamless integration between services.
- Rely on data models and ontologies (such as oneM2M or W3C Web of Things) that provide consistent structure and semantics across devices. A well-integrated system allows for better data flow, easier scaling, and reduced vendor lock-in.
- Follow a Reference Architecture
Leveraging an established reference architecture ensures your system is built on proven patterns and aligns with industry best practices. Reference architectures help:
- Managing devices and their data
- The device management aspect of a reference architecture is concerned with managing devices, their identity, and their lifecycles. Reference architectures describe:
- Device onboarding (registry and identity)
- Update management and deployment
- Configurations management
- Remote control with operations like disabling, enabling, or decommissioning devices
- The device management aspect of a reference architecture is concerned with managing devices, their identity, and their lifecycles. Reference architectures describe:
- Connectivity and communication
- Managing connectivity and bidirectional communication between devices, between devices and gateways, and between gateways and cloud services and applications is another key capability that is often described within IoT reference architectures. For edge computing, event-driven architectures are a good choice, with communication between devices and services using publish/subscribe protocols and message brokers.
- Analytics and applications
- To derive value from the data that comes from IoT devices, cloud applications provide visualization and analytics tools that operate over streams or batches of data to identify actionable insights. Depending on the use case, decision management and business process tools can trigger alerts or carry out actions in response. These frameworks often include templates for device-to-cloud data flow, edge processing, analytics pipelines, and more.
Conclusion
The combination of layered architecture, proactive security, operational automation, interoperable design, and reference models creates a strong foundation for any IoT solution. For example, in applications involving edge analytics, data flows efficiently from sensors through local edge nodes to cloud platforms where it's further processed or visualized. At the same time, security protocols ensure trust, automation streamlines updates and incident response, and standardized interfaces enable smooth expansion or integration with third-party systems.